NOTICES
PENNSYLVANIA PUBLIC UTILITY COMMISSION
Identity Theft; Doc. No. M-00041811
[35 Pa.B. 5594] Public Meeting held
July 14, 2005Commissioners Present: Wendell F. Holland, Chairperson; James H. Cawley, Vice Chairperson; Bill Shane; Kim Pizzingrilli; Terrance J. Fitzpatrick
Order By the Commission:
By order entered October 14, 2004, the Commission initiated an investigation pursuant to Sections 331(a), 501(a) and 1501 of the Public Utility Code, 66 Pa.C.S. §§ 331(a), 501(a) and 1501, to examine: (1) the impact of identity theft on Pennsylvania utility companies and consumers and (2) whether existing rules, regulations, and policies adequately protect consumers and utilities from the effects of identity theft. The order was served on all major jurisdictional companies to solicit comments from the utilities on a number of issues including: (1) utility procedures and processes to verify customer identities; (2) policy and procedures related to the use of an applicant or customer's social security number; (3) policies and procedures to protect privacy of customer account information and personal information; and (4) identity theft related incidences and losses.
The Commission served 123 jurisdictional utilities with interrogatories. The utilities filed responses to the Commission's interrogatories. Commission Staff reviewed the comments and responses and prepared a preliminary report which described the issue of identity theft as it relates to utilities and how Pennsylvania utilities are addressing the situation.
Based upon this report, as well as a review of the filed comments, it appears that, with respect to public utilities, there are four methods of identity theft: (1) person-to-person identity theft, (2) identity theft by utility employees, (3) name game identity theft, and (4) security database breach.
The first area of concern is the most publicized and familiar. This problem involves the unauthorized use of someone's identity by another person. According to the responses, an overwhelming majority of public utilities in Pennsylvania have not experienced many problems with person-to-person identity theft for the years 2000-2003. Moreover, of those reported cases of identity theft during this time, the vast majority reported less than a total of five cases.
The second method involves identity theft by employees when a utility employee gathers information about utility customers either directly or through the company's files and disseminates that information to an outside source, thereby giving that source access to the personal information of numerous customers. It is this problem, the unlawful use and dissemination of personal data maintained by utilities, that poses the greatest threat of exposing utilities and their customers to financial difficulty and civil liability.
Many utilities and employees have access to the personal information of its thousands of customers. As evidenced by recent security breaches of major companies such as Lexis-Nexis, there is no fail-safe system for protecting customers from identity theft perpetrated by a company employee. Nor is there a fail-safe system to prevent a computer hacker from entering a company system and stripping it of confidential information.
The third method is name game identity theft. This occurs when a household member uses the identification of another household member to establish a utility account and obtain utility service. In most cases, the ''victim'' and the perpetrator live in the same household and both benefit from access to the service. The real concern is that the utility often fails to recover the earlier debt. This means that the utility's ratepayers are burdened with the uncollectible debt.
It has been suggested that the newly enacted Chapter 14 of the Public Utility Code, 66 Pa.C.S. Ch. 14, may reduce the opportunity for customers capable of paying to avoid payment of utility bills by switching the names on their accounts. The definition of ''applicant'' and ''customer'' under Chapter 14 includes not only the person who is currently receiving the residential service, but also any adult occupant whose name appears on the mortgage, deed, or lease of the property for which residential utility service is requested.
Utilities commented that Chapter 14 is intended to seriously inhibit identity theft attributable to instances of the ''name game.'' Chapter 14 gives utilities tools so a nonpaying customer can no longer switch the account into the name of another person living in the household.
The fourth method of identity theft involves security database breaches by third parties (non-utility employee). To date, no reported or announced incidences of this type of identity theft have involved Pennsylvania jurisdictional utilities. Public utilities gather, access, and maintain confidential personal information on a regular and on-going basis. It is imperative, therefore, that this information be protected against theft and misuse. We note that the Federal Trade Commission1 as well as many states2 require that companies notify affected individuals of security breaches. In Pennsylvania, legislation was recently introduced to address identity theft concerns such as notification of security breaches and the protection of social security numbers. See, e.g., Senate Bill 712/House Bill 1023; Senate Bill 601; Senate Bill 180; Senate Bill 711; Senate Bill 714; and House Resolution 3513 .
In its investigation, the Commission also asked utilities whether the Commission's existing rules and regulations adequately protect consumers and utilities from the effects of identity theft and what changes, if any, should be made. Many utilities responded that current Commission regulations were sufficient to safeguard against identity theft and were not in need of modification. While some utilities proposed changes or modifications to the Commission's regulations,4 it should be noted many of the regulations referenced5 will be reevaluated as the Commission implements Chapter 14 legislation. 66 Pa.C.S. §§ 1401--1418.6
While the responses filed in this investigation proceeding indicate that identity theft incidences for Pennsylvania jurisdictional utilities with respect to person-to-person, employee identity theft and name game identity theft do not represent substantial numbers at this time, it is imperative that companies be particularly mindful of potential security database breaches. As evidenced by recent security breaches of major companies, effects of such breaches can have far reaching consequences on thousands of consumers.7
We note that there are millions of utility customers in Pennsylvania. Utilities collect and store the personal information of their customers on a daily basis. This information, if compromised or breached, could have a devastating impact on both the utility and its customers. There are additional steps utilities can take to enhance the protection of personal information. For example, utility companies are strongly encouraged to develop and re-evaluate their notification of breach procedures and their initial policies to ensure that storage of customer confidential information, either on company database or on outsourced arrangement, complies with federal and other relevant laws. Such preventative proactive measures protect consumers as well as the utility.8
Based upon responses and comments submitted in this proceeding as well as the Staff's report, we conclude that revisions to existing Commission rules and regulations may be premature at this time. However, with regard to Chapter 56 regulations, it is anticipated that this issue will be addressed, as warranted, during the regulatory review necessitated by Chapter 14. New legislation may be implemented which addresses identity theft. At that time, the Commission should then determine whether existing rules and regulations are consistent with the new law. To that end, Commission Staff is hereby directed to continue to monitor, on an on-going basis, identity theft related legislation and to make recommendations, as appropriate, regarding any future Commission action that may be warranted.
Moreover, to provide assistance to the legislature, consumers and utilities, the findings of Staff's preliminary report will be made public. In this way, the Commission in cooperation with the legislature and the utilities it regulates can work together to address this very important issue of identity theft; Therefore,
It Is Ordered That:
1. The Commission's Law Bureau monitor and evaluate federal and state legislation addressing identity theft and identity theft related issues and make recommendations, as appropriate, regarding any future Commission action that may be appropriate.
2. Findings of the Staff Preliminary Report be publicly released.
3. Copies of this order be served on, the Office of Trial Staff, the Office of Consumer Advocate, the Office of Small Business Advocate, and the Pennsylvania Office of Attorney General.
4. A copy of this order be published in the Pennsylvania Bulletin.
5. That this docket be marked closed.
JAMES J. MCNULTY,
Secretary
Staff Report on Identity Theft and Its Impact on Pennsylvania Utilities and Customers; Doc. No. M-00041811 Prepared by the Pennsylvania Public Utility Commission Law Bureau
Dated: May 24, 2005
TABLE OF CONTENTS I. INTRODUCTION
II. DEFINITION OF IDENTITY THEFT
III. OVERVIEW
A. Identity Theft Statistics
IV. PERSON TO PERSON IDENTITY THEFT
Analysis
V. IDENTITY THEFT BY UTILITY EMPLOYEES
A. Analysis
B. Preventative Measures
1. Employee Screening
2. Training
3. Ethics Policy
4. Management Employees
5. Information Technology Safeguards
VI. NAME GAME IDENTITY THEFT
VII. COMPANY RECOMMENDATIONS
VIII. CONCLUSION
IX. ATTACHMENTS
1. Attachment A (Questions)
2. Attachment B (National Identity Theft Fraud Statistics) (2004)
3. Attachment C (National Phone or Utilities Fraud)
4. Attachment D (Identity Theft Types Reported by PA Victims)
REPORT ON IDENTITY THEFT SUMMARY
By Investigation Order, entered October 14, 2004, at M-00041811, the Commission initiated an investigation to focus on identity theft, its impact on Pennsylvania utility companies and consumers, and whether existing Commission rules, regulations and policies adequately protect consumers and utilities from the effects of identity theft. In the order, the Commission directed all major jurisdictional fixed utility companies, telecommunications service providers, electric generation suppliers, and natural gas suppliers to file written responses to a specific set of questions prepared by the Commission pertaining to identity theft and invited interested parties to file written comments on identity theft.
The Commission served 123 jurisdictional utilities with interrogatories. All of the utilities that were served with the Commission's interrogatories filed responses. The majority reported that they had no identity theft incidents during the years 2000-2003. Moreover, of the utilities that reported cases of identity theft, the majority reported less than a total of 5 cases for those years. We suggest that one of the reasons identity theft in relation to Pennsylvania jurisdictional utilities rarely occurs is due to the fact that utility service is rendered to a specific service address. Because sufficient focus is on the residents of the service address, such thefts are relatively rare and are often discovered shortly after the account is established.
Although these numbers seem encouraging, utilities should be aware of the potentially devastating impact of identity theft and continue to implement or begin to implement effective procedures and practices to ward off identity theft. Utilities should be encouraged to utilize social security numbers in conjunction with credit agencies; to have policies and handbooks regarding employees' protection of confidential information; and to adhere to the Commission's regulations. Because utilities are regulated by the Commission, the Commission has the ability, through its rules and regulations, to require significant protections for the utilities and their customers.
I. INTRODUCTION
The Commission's Investigation Order states that ''[w]hile the Commission's ruling in a recent proceeding addressed the issue of one consumer's problem involving identity theft, the issue of identity theft as it relates to utilities and utility regulation warrants a more comprehensive review.''9 The Commission is concerned because on a yearly basis, thousands of individuals apply to Pennsylvania utilities and energy suppliers to initiate or transfer service, and the Commission's rules governing billing and credit policies10 were enacted prior to federal legislation and Federal Trade Commission (FTC) initiatives addressing identity theft. Because identity theft has become a national problem and the potential losses for both the utilities and their customers are significant, the Commission determined it was in the public interest to examine whether existing regulations and processes provide adequate protection against identity theft in Pennsylvania.
Pursuant to the Commission's authority under Sections 501, 504, 505, and 506 of the Public Utility Code,11 the Commission directed all major jurisdictional fixed utility companies, telecommunications service providers, electric generation suppliers, and natural gas suppliers to file written responses to a specific set of questions prepared by the Commission pertaining to identity theft. (The questions are attached hereto as Attachment A). The Commission also invited interested parties to file written comments on identity theft in relation to utility service and to propose solutions to address the problem, including amendments to the Commission's regulations pertaining to credit and billing practices.
In reply to the order, the Commission received a response from each of the 123 utilities that were served with the order. The Law Bureau reviewed and analyzed each response in writing this report.
In the area of public utilities, there are three major areas of concern that relate to identity theft; (1) person-to-person identity theft, (2) identity theft by utility employees, (3) name game identity theft, and (4) security database breach. This report will address each of these concerns and focus on the scope of the problem in Pennsylvania. This report will also address possible solutions to these problems, particularly in the area of prevention. By way of introduction to identity theft in general, this report will also define the topic and include relevant statistics on identity theft.
Due to the proprietary nature of the responses received from the utilities, the substance of this report will not contain the names of the parties responding, except in those limited instances where reference is being made to comments filed by a particular party.
II. DEFINITION OF IDENTITY THEFT
While identity theft has been depicted as one of the ''fastest growing crimes in the nation''12 and as ''the crime of the new millennium,''13 a 2003 FTC study indicates that identity theft has impacted only 4.6 percent of the population.14 In some areas, even when recommendations are made to implement methods to decrease identity theft occurrences, this is not regarded as an appropriate allocation of resources.15
In Pennsylvania, the crime of identity theft is defined as ''. . . the possession or use, through any means, of identifying information of another person without the consent of that other person to further any unlawful purpose.''16 At the outset, we note that the concept of identity theft in relation to utilities does not fit neatly into this definition. Utility service is rendered to a specific service address, and it is often difficult to discern if the service is rendered without the consent of the victim, particularly when the victim resides at the service address. These concepts will be discussed in further detail throughout this report, notably in Section VI.
Generally, identity theft refers to a variety of crimes which involve ''stealing someone's personal identifying information.''17 The identity thief uses a broad range of methods to obtain the information, from ''basic street theft to sophisticated, organized crime schemes involving the use of computerized databases or the bribing of employees with access to personal information on customer or personnel records.''18 The thief profits by using the victim's personal information to take funds from his/her bank account, create debts, or commit crimes.
III. OVERVIEW
Identity theft has become a growing concern in virtually every aspect of business relationships in today's society. A person must be readily able to prove who they are whether purchasing a home, utility service, boarding an airplane, or going to a physician. In fact, one's identity must be proven whenever it may be to the advantage of someone to impersonate another person.
Identity theft is not a new problem. For years, stolen wallets, mail, and checkbooks have been fertile grounds for thieves to take on another person's identity and benefit from it. Moreover, these crimes were prevalent long before the widespread usage of computers and other modern technological advances.
Based on the FTC's 2003 report, a victim is likely to know the identity thief when the crime is serious. In 26 percent of the cases, the victim knew the thief's identity. In 35 percent of these cases, the thief was a family member or relative.19
In response to the problem of identity theft, numerous state and federal laws have been enacted. Forty-four states have specific laws criminalizing identity theft, and five other states have laws that cover activities included within the definition of identity theft.20
The federal government has also attempted to address this problem. The federal Identity Theft and Assumption Deterrence Act of 1998 specifically labels identity theft as a crime.21 The Act criminalizes the unauthorized use or transfer of identity documents such as social security cards and the unauthorized use of credit cards and ATM codes, as well as instances when a person ''knowingly transfers or uses, without lawful authority, a means of identification of another person with the intent to commit, or to aid or abet, any unlawful activity that constitutes a violation of Federal law, or that constitutes a felony under any applicable State or local law. . . .''22
The Federal Fair and Accurate Credit Transactions Act of 2003 (FACT Act)23 focuses on credit reporting agencies and the use of credit reports and credit scores. It requires businesses engaging in commerce to establish procedures to respond to consumer claims of identity theft. It also deals with numerous other issues, such as the ability to sell or transfer debt involving identity theft; what may be printed on receipts for credit or debit cards; how change-of-address requests for credit or debit cards may be processed; sharing of consumer information among affiliates; and limitations on the use of medical information. Additionally, Congress passed the Identity Theft Penalty Enhancement Act24 on July 15, 2004, to prescribe stricter penalties for the commission of identity theft and fraud.
There are two variables that make identity theft so much more dangerous to our society today than it was before. These factors have made identity theft a potential threat to virtually everyone.
The first of these variables is the use of computer data. The widespread use and accessibility of computer data clearly has the potential of expanding the operation of identity thieves. This is especially true if the perpetrator has, or purchases, access to databases that hold confidential information.
The second variable is the advancement in technology that enhanced the ability to fraudulently duplicate identity documents. These advances have made the duplication of identification documents such as driver's licenses, social security cards, passports, etc, of such quality that these counterfeit documents have become increasingly more difficult to detect.
Another aspect of technology that has caused identity theft concerns is the widespread usage of telephone communications to apply for and order changes to utility service. In fact, most of the utilities responding to the interrogatories process most of their applications and service inquiries over the telephone. Many have limited office hours available to the public and many never physically see the applicants.
Concerns over identity theft have affected the manner in which public utilities conduct their businesses. In fact, the utility industry ranks second (though a very distant second) only to the credit card industry in frequency of this type of identity theft.25
A. Identity Theft Statistics
On February 1, 2005, the FTC released its annual report, National and State Trends in Fraud & Identity Theft: January--December 2004, analyzing consumer complaints regarding identity theft.26 Identity theft topped the list of categories of fraud-related complaints filed with the FTC in 2004, amounting to 39 percent of the 635,173 consumer fraud complaints filed with the agency.27 The national statistics reported that credit card fraud was the most common form of identity theft at 28 percent, followed by phone or utilities fraud at 19 percent.28 (See detailed National Identity Theft Fraud Statistics (2004) at Attachment B). The 19 percent of consumer complaints relating to phone or utilities fraud is made up of 10 percent attributable to new wireless accounts; 5.9 percent attributable to new telephone accounts; 4.2 percent attributable to new utilities accounts; 0.7 percent attributable to unauthorized charges to existing accounts;29 and 0.3 percent attributable to unspecified accounts.30 (See Attachment C: Nat'l Phone or Utilities Fraud).
The Pennsylvania statistics followed the federal statistics with credit card fraud the most common form of identity theft at 32 percent, followed by phone or utilities fraud at 19 percent.31 (See Attachment D: Identity Theft Types Reported by PA Victims). Among the major metropolitan areas for identity theft-related complaints, Philadelphia-Camden-Wilmington area was ranked 29th with 4,782 victims and Pittsburgh was ranked 49th with 1,211 victims.32 When categorizing identity theft victims by state, Pennsylvania was ranked 25th with a total of 7,563 victims.33 The top identity theft victim locations in Pennsylvania were as follows: Philadelphia (1,871 victims); Pittsburgh (453 victims); Allentown (124 victims); Reading (112 victims); York (112 victims).34
The results of the FTC's 2003 Identity Theft Survey Report, suggest that almost 10 million individuals within the United States were victims of some form of identity theft within the previous year.35 In evaluating the costs of identity theft, the study found that the total loss to businesses and financial institutions was $47.6 billion, and the total loss to victims was $5 billion.36
According to the Pennsylvania-specific data provided in the FTC's Identity Theft Victim Complaint Data: Figures and Trends in Pennsylvania--January 1--December 31, 2003, identity theft regarding phone or utilities fraud accounted for 21 percent of the total number of victims reporting identity theft.37 In that study, the 21 percent of phone or utilities fraud was broken down as follows: new wireless accounts (11.2 percent); new telephone accounts (3.6 percent); new utilities accounts (4.6 percent); unauthorized charges to existing accounts (0.7 percent); unspecified (0.6 percent).38
In analyzing the number of identity theft victims per state, Pennsylvania was ranked 24th with 6,545 victims.39 The top cities in Pennsylvania based on the number of identity theft victims during the covered time period follow: Philadelphia (1,639); Pittsburgh (367); Allentown (98); West Chester (79); Harrisburg (74); and York (74).40
IV. PERSON-TO-PERSON IDENTITY THEFT
Analysis
The first area of concern is the most publicized and familiar. This problem involves the unauthorized use of someone's identity by another person. It should be noted, however, that the most common form of this type of identity theft occurs when a household member uses an identification of another household member to establish a utility account and obtain service. This will be discussed more fully in Section VI in this report, Name Game Identity Theft.
Public utilities in Pennsylvania have not experienced many problems with person-to-person identity theft. In fact, the overwhelming majority of the responding utilities reported that they had experienced no identity theft incidents for the years 2000 through 2003. Moreover, of those reported cases of identity theft during this time, the vast majority reported less than a total of five cases. Even where a utility reported more than five total cases, the utility clarified that identity theft cases are not tracked separately and that the total included all fraud that the company had experienced during those years and not just identity theft which may, or may not, have accounted for some of those cases.
Presently, most Pennsylvania utilities do not view identity theft as a significant problem. This is probably due, in large part, to its very rare occurrence. But we would suggest that another reason for this review is that, in relation to losses to the companies, this type of identity theft is usually discovered within several months of the account's being created. Because the service is rendered to a specific service address, this type of theft is usually discovered shortly after the account is established and sufficient focus is on the resident of the service address.
These results raise the question whether identity theft is really the ''new crime of the millennium'' or just a minor problem that the media has dramatized.41 It is suggested that the answer to this query is that, although person-to-person identity theft in the utility industry is, at present, a relatively minor problem that draws an over abundance of media attention, this problem has the potential to become one of the utility industry's most prevalent fraud concerns.
At the outset, it should be made clear that, although this type of identity theft appears to be rare in the utility industry at the present time, no one wants to be a statistic included in the ''victim'' column of an identity theft study. The individual victims of identity theft often expend many hours of time and a great deal of effort in rectifying the problems that this type of crime causes. In some cases, money is lost and credit reports are adversely affected. This fact alone should make it imperative that all possible measures to protect a utility customer's identity should be taken.
It is often forgotten that person-to-person identity theft involves another victim other than the person whose identity is stolen. The other ''victim'' of identity theft that is often overlooked is the utility to which the stolen identity is presented. This victim may be forgotten due to the fact that the media does not seem very interested in a utility company's being duped into serving the wrong customer for a short period of time. Utilities are generally looked at as having ''deep pockets.'' While it may be true that the very small numbers of identity thefts that have been perpetrated through Pennsylvania utilities is somewhat insignificant at present, the potential effect could, eventually, be dramatic.
It must also be remembered that a public utility has many customers and each of those customers has provided some type of personal information to the utility to initiate service. Therefore, unless the company has some reliable way to identify its customers, numerous instances of identity thefts are possible. Moreover, it is apparent that when a customer files a complaint that someone else has used his identity and the complaint is verified, the utility always takes the loss. Of course this loss is not borne by the company's stockholders, but is passed on to the utility's customer base so that everyone is affected.
As stated previously, a review of the data submitted by the utilities clearly indicates that person-to-person identity theft is not seen to be significant in Pennsylvania at the present time. However, the data reveals that there may be a reason for this low occurrence of this type of identity theft.
After examining the responses presented, it becomes apparent that the key factor in the frequency of person-to-person identity theft is the utilization by many utilities of social security numbers as an identification tool, coupled with the utilities' use of credit agencies and those agencies' positive identification programs. According to the utilities that rely on these methods, incidents of identity theft are minuscule.
If one questions whether the use of social security numbers and credit agencies are the real cause for the low occurrence of identity theft, or whether this type of fraud is just rare in general, one need only to review the interrogatory answers of a large jurisdictional utility that utilizes this method. This particular utility is representative of a group of companies that utilize social security numbers and credit agencies to verify identities.
This utility reported that the numbers of attempted identity thefts for the years in question were:
2000--130
2001--143
2002--165
2003--1269In its answer to the interrogatories, the company stated:
[The Company] utilizes the EQUIFAX (Positive Identification Program (P0510) to identify potential instances of identity fraud. The EQUIFAX Positive Identification Program is a consumer database of information created and updated by a credit inquiry, normally based on credit related activities or employment verification of an individual.Anytime a consumer applies for gas service, [the Company] requests the applicant provide their social security number. [The Company's] customer service representative keys the social security number provided by the applicant, into a computer program. The computer program transmits the information to EQUIFAX. EQUIFAX scans their social security index database to determine the name of the person attached to the social security number provided by the applicant.A second scan of the social security number provided by the applicant is made on the EQUIFAX SAFESCAN database. This valuable segment of the POSID program is used to identify attempted fraud. EQUIFAX's database includes data from the Social Security Administration that identifies ''out of range'', ''deceased,'' or ''retired'' social security numbers, as well as social security numbers identified as ''minors.'' Suspicious activity is also collected and reported from various sources via EQUIFAX including names of other people who have used the same Social Security number the applicant provided.Within seconds, EQUIFAX provides information with regards to the legitimacy of the applicant's identification. If EQUIFAX verifies the exact match of the social security number to the exact spelling of the customer's name, the company representative will proceed with scheduling the service connect order. However, if the information provided by the applicant fails the POSID verification test, the customer service representative will immediately deny the applicant service and request further identification be provided. [The Company] will issue a denial of service letter to the applicant requesting a notarized affidavit and a residential gas service application be completed.The significance of this method becomes apparent when one realizes that, although a relatively large number of identity thefts were attempted for the years in question the number of actual identity theft complaints the company received were:
2000--0
2001--5 (four of which were unfounded)
2002--2 (both were unfounded)
2003--2 (one was unfounded)Simply stated, for the years in question, there were 1,707 potential attempts to commit identity fraud through the use of questionable social security numbers. However, the company only actually experienced two verifiable incidents of identity theft for those years in question. Obviously, the company's method of identifying its applicants made it possible to detect an identity problem at the outset. These preventative measures effectively neutralized these threats.
Though most of the companies that responded to the interrogatories did not go into the same amount of detail as this particular utility, it seems that many companies, whether urban, suburban, or rural, used some similar method of identification. The use of a social security number is a readily available ''red flag'' to warn a utility that there may be a problem.
Virtually all the utilities state that an applicant's refusal to provide a social security number does not prevent an applicant from receiving service. However, where a social security number is not provided, or where one is provided and fails to verify the person's identity, most utilities require the applicant to personally appear before a company employee and present at least two forms of identification. Two of the companies encode the person's account with a personal password such as the applicant's mother's maiden name or a personal identification number.
Most of the companies require customers to provide a social security number or account number along with the customer's telephone number and address when seeking access to their accounts. However, when a transfer of service is requested, nearly all of the companies only permit the person listed as the current customer to transfer the service. Apparently, these procedures have also been effective in preventing identity theft.
The Pennsylvania Telephone Association (PTA) filed comments in response to the Commission's Order. In its comments, PTA suggested that the Commission should recognize that the FTC enacted rules pursuant to the FACT Act that went into effect on December 1, 2004. Therefore, PTA urged the Commission to delay any actions regarding identity theft until the full effect of the FTC's rules could be determined.
The PTA also cautioned the Commission that utility companies in Pennsylvania can be found at both ends of the business spectrum. PTA stated that some utilities are small family-owned operations that serve rural areas and whose employees personally know a significant portion of their customers and have never had an identity theft incident. Correspondingly, other utilities are listed on stock exchanges and lose significant amounts of money and man hours to identity theft. Therefore, PTA suggested that any action taken on a state-wide level must grant a certain degree of flexibility so as to be effective, but not oppressive, to different types of customers and utilities.42
In addition to the responses to the interrogatories filed pursuant to the Commission's Order, a large telecommunications company also filed additional comments through its counsel. The company expressed concern that the Commission carefully analyze the projected costs versus the potential benefits realized by placing additional regulatory constraints on public utilities operating in Pennsylvania.
The company also added that additional regulatory oversight may not be prudent because consumers in Pennsylvania already have multiple levels of protection from identity theft available to them. The company stated that this is particularly true with respect to telephone utilities since the Commission has implemented 52 Pa. Code § 63.131, et seq., as these regulations establish rigid safeguards for protection of confidential telecommunications information. The company also cited other statutes that it submits protect Pennsylvania consumers from identity theft.
Conversely, many of the utilities, in response to question 15,43 suggested that many of the Commission's identity theft regulations are obsolete and should be changed to provide for more protection. These responses will be addressed later in this report. However, it is interesting to note that a large telecommunications company suggested that 52 Pa. Code § 64.32 (credit standards) should be changed so that, as a condition of providing service, and to determine identity and credit worthiness, utilities should have the authority to ask applicants for five (5) pieces of identification.
Another advantage to medium and large utilities utilizing credit reports in conjunction with social security numbers is that information relating to identity theft can be easily retrieved and analyzed. One problem that utility companies seem to have is that they do not distinguish between identity theft and all other fraud complaints. Through many of the credit reporting company's data bases, information can be received to determine exactly how many attempted cases of identity theft a company may be experiencing.
Although the most effective way for most utilities to combat identity theft seems to be the use of social security numbers and credit reporting agencies, some smaller utilities may not have the ability or the resources to utilize these services. In response to the interrogatories, one small telecommunications company stated that the majority of its employees live and have deep roots within its service territory and that most of the customers are known by name. However, this company still has policies and procedures in place to insure the customer's identity. One of the cornerstones of this identification process is that the customer is required to complete the company's application in person at one of its offices. During that time, some form of identification, preferably a photo identification is presented.
V. IDENTITY THEFT BY UTILITY EMPLOYEES
A. Analysis
Employee identity theft involves a utility employee gathering information about utility customers either directly or through the company's files and disseminating that information to an outside source, thereby giving that source access to the personal information of numerous customers. It is this problem, the unlawful use in dissemination of personal data maintained by utilities, that poses the greatest threat of exposing utilities and their customers to financial difficulty and civil liability. Public utilities gather, access, and maintain confidential personal information on a regular and on-going basis. It is imperative, therefore, that this information be protected against theft and misuse.
Unlike person-to-person identity theft, where suspicion is generated relatively soon after the theft, employee identity theft may take a long period of time to detect. In fact, it may not be detected by the customer until the customer learns that he has financial obligations about which he did not know or the customer receives a credit report indicating fraudulent activity. By that time, all the turmoil and expense that results from the use of a customer's identity has already been borne by customer. This can have a devastating effect.
On the other hand, a public utility's actual monetary losses due to this kind of identity theft may be somewhat hard to calculate. In most instances, the utility would not be out-of-pocket any revenues because the customer is probably paying his utility bills, but simply does not know that his identity is being used for other expenses or purposes that do not directly effect his relationship to the utility. The utility's exposure for financial harm may come by way of civil liability for failing to adequately protect the confidential information of their customers. In the long run, this could be considerably more damaging to the utility than simply writing off an individual's utility bill.
In reviewing all of the responses from the utilities that answered the Commission's interrogatories, employee identity theft appears to be even rarer than person-to-person identity theft. In fact, the only verified incidents of this type of utility theft were reported by a medium- sized utility in the Scranton area. The company learned of the incident, fired the employee, and had the employee prosecuted criminally. The employee was convicted of a felony and is currently being sued civilly by the victim. It should be noted that this case was on a very small scale and occurred because the employee's name was the same as the victim's name so the employee decided to take advantage of the victim's confidential information.
As is the case with person-to-person identity theft, employee identity theft, while apparently not a significant issue at the present time, has the potential to become an enormous problem if utilities do not take reasonable measures to protect customers' confidential information. This is especially true if utilities are permitted to require social security numbers. The task is then to determine the most effective ways to protect confidential customer information.
In reviewing the companies' responses to questions regarding their policies relating to employee identity theft, many companies had specific portions of their handbooks address the handling of confidential information and policies relating to employee fraud in this area. However, some of the smaller companies had no such policy because they had never experienced employee identity theft. Most of these smaller companies indicated that they would refer the matter to law enforcement.
At the outset, it must be understood that there is no fail-safe system for protecting customers from identity theft perpetrated by a company employee. Nor is there a fail-safe system to prevent a computer hacker entering a company system and stripping it of confidential information. The utility companies, especially larger ones, face a constant battle to upgrade their computer systems with protective devices to guard against computer hackers who damage these systems and retrieve confidential customer information. However, based upon the companies' comments, some actions do limit the amount of exposure a utility might have to identity theft by a company employee.
After carefully reviewing the interrogatory responses and speaking with a number of company officials, in particular those of a large urban utility, an on-going multifaceted approach to protect confidential information is the most successful action. The best way to achieve this is to promote a well informed and honest workforce, regardless of the size of the utility.
B. Preventative Measures
1. Employee Screening
As the companies indicated, the first step is to create a work force that can be trusted to protect confidential information that is provided to the company by carefully selecting employees. The companies suggest that pre-employment background checks should be conducted on all potential employees. This includes a criminal records history check and affirmative statements by the employee concerning his or her criminal history. A company does not hire anyone convicted of a crime of dishonesty or the illegal use or sale of contraband or controlled substances. The companies have found that in order for utilities to conduct business, they must be able to protect information from theft or misuse and, therefore, the utilities must maintain strict guidelines concerning who will be hired to properly handle and protect this information.
The companies stated that it is important that all employees are scrutinized through this type of check. Moreover, this is a routine screening that can be accomplished by a large or small company through the use of computer technology. Specifically, the screening generally includes the following:
a. Verification that all information on the employment application and supporting documentation is accurate and current;
b. Requesting all information to conduct a thorough criminal history record check;
c. Taking and retaining copies of application information such as birth certificates, driver's licenses, and social security cards;
d. Reference checks;
e. Verification of education.
This type of background verification helps to insure that utilities know the type of employees that are in their workforce.
2. Training
New employees receive extensive training on the utility's privacy policy and how to maintain confidential records. Many of the companies responding to the Commission's interrogatories incorporate this training with their employee orientations. This may suffice for some employees that are taking information over the telephone, but more extensive training is required of those employees who are entrusted to protect and preserve confidential information.
3. Ethics Policy
Most of the major companies have adopted a corporate ethics policy concerning conflicts of interest and using the corporation for one's personal gain. The companies indicated that merely having an ethics policy and handing out a booklet is not enough. At the very least, the companies have found that they should also provide some type of basic training on their ethics codes to define terms and state their expectations, particularly with regard to customer confidentiality.
Along with educating employees on the companies' ethics codes, the companies strictly and aggressively enforce their codes. Strict enforcement is accomplished by:
a. Terminating employees who intentionally misuse confidential customer data, and where appropriate, the company should utilize local law enforcement;
b. Terminating employees, who during the course of their employment, are convicted of crimes of dishonesty or other moral turpitude;
c. Actively investigating any allegations of dishonesty and terminate such employee if the investigation determines it is likely that the employee committed the act;
d. Where necessary, utilizing outside investigation services to conduct a full and thorough investigation;
e. Establishing a policy of publicizing the company's strict ethical standards, and the actions taken when those standards are violated; and
f. Vigorously opposing unemployment compensation claims when employees are terminated for dishonest activities.
4. Management Employees
The Companies stated that in order for a utility to effectively combat employee identification theft, management employees should be held to a higher standard of conduct than rank and file employees. This does not mean that rank and file employees can ignore or disobey an ethics policy. In fact, it means that management employees should be responsible, not only for their own compliance with ethics policies, but also for closely scrutinizing the employees they supervise, to insure that ethical standards are being met. Additionally, the hiring of management level employees, or employees who will be directly involved with the accumulation and storage of confidential information, should, at the outset, be more closely scrutinized. Simply stated, when hiring or promoting employees to a management position, or one of trust, a more extensive background check should be conducted.
Many of the larger utilities have developed different procedures for screening confidential employees. One very large natural gas company was particularly helpful in sharing its procedures. After reviewing this company's responses to the interrogatories, as well as its procedures, and personally speaking with its corporate counsel, it appears that the way it screens its confidential employees is very effective. Specifically, in addition to the steps for pre-employment screening previously enumerated in this report, this company does the following:
a. Lexis-Nexis Check
1. Lien and Judgment Index
2. Newspaper and Magazine files
3. Property Ownership, Property Transfer and Tax Assessor files
4. Federal and State Criminal and Civil Docket files
5. Bankruptcy file
6. Federal and State case files (Lexis)
7. SmartLinx TM Person and Location tool
8. All Find tool
9. Business and Corporation files
10. Social Security Death Index
b. Check of local court docket where appropriate
c. Check with federal, state, and local law enforcement agencies where appropriate
d. Internet name search
e. Prior bad acts (honesty and integrity related acts that may not have resulted in arrest or conviction)
5. Information Technology Safeguards
Protecting a customer's confidential information is a two-fold problem. First, as stated previously, companies find it necessary to closely scrutinize the employees handling such information. The second problem is the on-going battle of utilities to protect hardware, software, and data from intrusion, destruction, and file corruption.
Those companies that utilize computer systems to obtain, maintain, track, and store confidential customer information do whatever is technologically possible to protect that information. This includes:
a. Firewalls
b. DMZ
c. Paper trail when employee modified files
d. Network monitoring tools-monitor fire wall activity and all of the network devices
e. Regular security assessments
f. Employee education and awareness
g. Staying current with best practices on handling and protecting data
h. Protection against viruses and malicious code (all desktops and servers)
i. Maintaining a technical disaster recovery plan in place
j. Following current practices for backing up data and sending it off- site
k. Stratifying access and viewing rights based on need to know
While it is recognized that some of these methods for protecting customers against employee identification theft may be costly and time consuming for smaller utilities, the companies indicated that it is necessary.
A few of the smaller utilities still store confidential information in file cabinets. These companies state that these file cabinets are locked and only certain employees have access to them. Although the use of locked file cabinets may be outdated, and is not encouraged, it is probably preferable to utilize secure file cabinets instead of an unsecured computer system. This is because file cabinet information may be stolen only by physically entering a company's facilities and removing the files. On the other hand, an unsecured computer system allows an identity thief access to confidential files and selling the information found in those files without ever leaving the comfort of his computer lab.
After reviewing the companies' responses to the interrogatories it appears that careful hiring practices, employee training, establishing company policies and strict enforcement of those policies are the best ways to combat employee identity theft. Although no system is 100% effective, utilization of these methods seems to significantly decrease the threat of employee identity theft.
VI. NAME GAME IDENTITY THEFT
This is a third type of fraud that some utilities classify as identity theft. While name game identity theft may or may not constitute identity theft under Pennsylvania Crimes Code 18 Pa.C.S. § 4120, it is nonetheless an activity of serious concern to fixed utilities in Pennsylvania and warrants discussion in this report.
Name game identity theft occurs when a household member uses the identification of another household member to establish a utility account and obtain utility service. In most cases, the ''victim'' and the perpetrator live in the same household and both benefit from access to the service. For this reason, and because family members rarely prosecute each other for this form of identity theft, discovery rarely, if ever, results in prosecution. The problem with name game identity theft is not the individual ''victim's'' losses because that person benefits from the theft by living in the home where the utility service is being provided. The real concern is that the utility often fails to recover the earlier debt. This means that the utility's ratepayers are burdened with this uncollectible debt.
According to the Commission's Bureau of Consumer Services (BCS), which contributed significantly to this section of this report, name game identity theft is most often reported by fixed utility companies. However, it is apparent from the answers to the Commission's interrogatories that the utilities, in most cases, did not classify name game identity theft as a type of identity theft in answering the interrogatories.
Of course, not all instances of the ''name game'' meet the definition of identity theft because the ''victims'' may collaborate with the ''perpetrators'' to receive utility service. However, identity theft may still occur in those situations where there is a request to place the service in a person's name who has not consented to the use of his name and personal information such as his social security number.
To combat this type of identity theft, Title 66 was amended by adding Chapter 14, 66 Pa.C.S. §§ 1401, et seq. Chapter 14 is intended to eliminate the opportunities for customers capable of paying to avoid payment of utility bills by switching the names on their accounts. This is accomplished by including within the definition of ''applicant'' and ''customer'' not only the person who is currently receiving the residential service, but also any adult occupant whose name appears on the mortgage, deed, or lease of the property for which residential utility service is requested.
Additionally, Chapter 14 permits utilities to require that the applicant provide names of each individual occupant residing at the location and proof of his identity. Moreover, Chapter 14 allows a public utility to require the payment of an outstanding balance, or portion of an outstanding balance, if the new applicant resided at the property for which services were requested during the time the outstanding balance accrued, and for the time the applicant resided there.
Chapter 14 is intended to seriously inhibit name game identity theft attributable to instances of the ''name game.'' A nonpaying customer can no longer switch the account into the name of another person living in the household.
VII. COMPANY RECOMMENDATIONS
The last question posed by the Commission asked utilities whether, in their opinions, Commission regulations create an opportunity for identity theft. Additionally, those utilities that envision a problem with the regulations were asked to propose changes. Due to confidentiality concerns, these responses will be discussed without specifically identifying the utilities.
Many of the utilities that responded to this question opined that the current regulations were sufficient to safeguard against identity theft and were not in need of modification. These utilities did not have a problem with identity theft and were in general agreement that if utilities adequately uphold the Commission's regulations and conduct a sound business practice, identity theft should not be a major concern.
As stated previously, one major telecommunications utility and PTA agreed with this general sentiment and focused on the costs of additional regulations, coupled with the increased administrative burden that the regulations might place on utilities, and cautioned that these factors must be weighed against any potential benefits to be gained. This company also stated that if the Commission were to implement regulations with high costs of compliance for public utilities, the end user consumers of telephone services would suffer negative consequences in the form of increased costs and this would inevitably lead to utility rate increases.
This utility also stated that in 1996, the Pennsylvania General Assembly enacted its own identity theft statute at 18 Pa.C.S. § 4120, which makes identity theft a crime in the Commonwealth that can rise to the level of a felony. In addition to other protections afforded by the federal government, such as limitations on the required use of social security numbers, the US Government recently enacted amendments to the FCRA, 15 U.S.C. § 1601, et seq. The amendments, known as the FACT Act, Pub. L. No. 108-159, 117 Statute 1952, were passed in 2003, with the express purpose of ''amending the FCRA to prevent identity theft. . . .'' The Act contains many new provisions to avoid identity theft, such as placing fraud alerts on consumer credit reports, allowing free access to consumer credit reports to those who have placed fraud alerts, and redaction of complete credit card numbers on customer receipts. This utility and others suggest that because this statute is fairly new, ample time must be allowed to gauge its effectiveness before additional levels of regulatory burden are imposed.
Nonetheless, this company suggested changing the Commission's regulations. Specifically, it suggested that, to assist in the fight against identity theft, 52 Pa. Code § 64.32(4)(ii)(A) be amended to remove reference to ''the applicant's social security number'' so that this number is not made available.
Other utilities also expressed concerns and made suggestions. For example, a major gas utility suggested that it is not wise to post notices on a customer's premises that include visible names and account numbers.
Another major jurisdictional telecommunications utility responded that § 64.32 (Credit Standards) does not specify use of credit bureau reports as a tool for an applicant to demonstrate credit worthiness. This utility believes that this opens the door for fraud by making it difficult to obtain and verify information regarding the applicant. Accordingly, it suggested that the Commission's regulations should work in cooperation with the FACT Act and the FCRA. To this end, the utility proposed that § 64.32 be revised to permit carriers to use credit reports as the primary standard for creditworthiness and that § 64.61 (Grounds for Suspension) be amended to allow the disconnection of utility service for fraud without notice and the ability to deny reconnection of utility service where the ground for suspension is fraud.
A relatively small telephone company stated that the Commission's regulations do not specifically address preventative measures that may guard against identity theft. This utility believes that requiring one personal visit to the office, two separate forms of proof of identity, including a photo ID and a copy of the customer's social security card should help minimize exposure to identity theft.
As mentioned previously, a major jurisdictional telecommunications utility suggested that changes be made to 52 Pa. Code § 64.32 (Credit Standards). Specifically, this utility feels that as a condition of providing service and to determine identity and creditworthiness, it is essential that it have the ability to ask for five (5) pieces of identification from applicants, including the requirement that applicants provide a social security number without restriction. Information that is necessary and should be required before provisioning service includes date of birth, employment, and address. It stated that, under the FACT Act, a social security number is crucial to make inquiries to one of the major credit bureaus in order to receive a Fraud Alert Indicator, where applicable.
Another indicator that would be provided by using a social security number would be a Notice of Address Discrepancy Indicator. Both of these indicators act as a ''red flag'' in protecting the real customer when inquiries are made to establish service without authorization. This utility also agreed with other responders that the existing Commission rules and regulations need to coexist and complement the FACT Act's provisions.
In its responses, a major water utility suggested that to strengthen 52 Pa. Code § 56.33, all applicants for utility service should be required to provide proof of identity (social security number, driver's license number, etc.). The utility further opined that a utility should be afforded discretion to deny utility service when an applicant refuses to comply with proof of identity requirements. With respect to §§ 56.16, 56.72, and 56.131, transfer of accounts, discontinuation of service and third party notification, respectively, the utility suggested that callers be required to provide a passcode or password in order to access account information.
Several energy utilities responded to the Commission's questions as well. A major gas utility suggested that the definition of ''unauthorized use of utility service,'' found at 52 Pa. Code § 56.2, be amended to expressly clarify that service acquired through identity theft is unauthorized. It also suggested that 52 Pa. Code § 59.26 be amended to expressly authorize a utility to refuse to serve an applicant who fails to provide sufficient proof of identity and residency. Lastly, this utility suggests that the general regulations be amended to allow utility security departments to openly communicate with and share information with each other regarding identity theft complaints. This type of communications would help security personnel verify information provided to them by the complainant and other witnesses/suspects.
These responses are representative of the responses received from interrogatories. It should also be mentioned that the Pennsylvania Telephone Association filed responses for numerous smaller telephone companies. Generally, these companies have not had any experience with identity theft of any kind.
VIII. CONCLUSION
In conducting a thorough review and analysis of identity theft and its impact on Pennsylvania utilities, the data shows that Pennsylvania utilities have not yet experienced significant identity theft problems. As stated earlier, the majority of utilities that responded to the Commission's interrogatories reported no identity theft incidents during the years 2000-2003. Moreover, of the utilities that reported cases of identity theft, the majority reported less than a total of 5 cases for those years. As suggested previously, one of the reasons identity theft in relation to utility service is rare is because the service is rendered to a specific service address and is usually discovered shortly after the account is established.
Despite the fact that identity theft in relation to Pennsylvania's utilities is currently a relatively minor problem, the problem could expand and become a more prevalent concern with potentially harmful affects on both utility companies and their customers.
The key reasons that person-to-person identity theft is not currently a large problem for Pennsylvania utilities are the utilities' utilization of social security numbers as an identification tool, coupled with the use of credit agencies and the agencies' positive identification programs. Additionally, the utilities' adherence to the Commission's regulations regarding the confidentiality of customer information aid in combating this problem.
Similarly, employee identity theft has not been identified as a major concern for most companies because many have detailed policies and employee handbooks regarding the handling of confidential information. It is recommended that all companies implement a multi-faceted approach to promote a well-informed and honest workforce, which includes employee screening, training, ethics policies, higher standards for management employees, and information technology safeguards. Moreover, to combat instances of ''name game'' identity theft, the General Assembly has amended Title 66 by adding Chapter 14, 66 Pa.C.S. § 1401, et seq.
Based upon the findings in the report, it appears that identity theft is not currently a major problem for Pennsylvania utilities. However, utilities should be aware of its potential impact and continue to or begin to implement effective procedures and practices to ward off identity theft. Utilities should be encouraged to utilize social security numbers and credit agencies; to have policies and handbooks regarding employee protection of confidential information; to adhere to the Commission's regulations; to apply any other effective procedures to ensure that confidential information is protected.
ATTACHMENT A All major jurisdictional fixed utility companies, telecommunications service providers, and electric generation suppliers and natural gas suppliers, are directed to file written responses to the following questions on identity theft44 :
1. Provide the total number of disputes, as that term is defined in Commission regulations45 , in which a customer alleged identity theft for each of the following calendar years:
(a) For the year ending December 31, 2000.
(b) For the year ending December 31, 2001.
(c) For the year ending December 31, 2002.
(d) For the year ending December 31, 2003.
If the company keeps statistics by fiscal year, please provide the above information for the immediate past four fiscal years.
2. Describe and provide a copy of company policy and procedures relating to verification of the customer's identity in the application process and the account transfer process. Also, provide information regarding the circumstances under which the company requests that a consumer provide additional sources of personal identification in order to verify that consumer's identity.
3. Describe and provide a copy of the company's written policy regarding new applications for service. Provide a copy of rules and regulations from the company's current and effective tariff relating to new applications for service, including circumstances under which written applications are required, and circumstances under which applications for service may be accepted over the telephone. Describe the process employed by the company to verify information provided over the telephone to ensure that the person requesting the service is in fact who he or she represents themselves to be.
4. Other than applications for new service, what kind of personal information is required when customers call in regarding their service and seeks to do the following?
a. Verify the balance due.
b. Transfer the account into another person's name.
c. Complain about a service disruption.
d. Pay the bill over the phone.
e. Ask questions about their bill or service.
f. Close an account.
g. Any other action not described above.
5. Describe and provide a copy of the company's policy relating to the use of an applicant's or a customer's social security, particularly the circumstances under which the company requires that a social security number be provided, and how the social security number is used by the company. Describe and provide a copy of all documents related to security measures that the company uses to protect a customer's social security number. Describe and provide a copy of all documents relating to the company's procedures and policy applicable to situations where a customer refuses or fails to provide a social security number. By way of example only, if the company declines to serve to a new customer, what is the basis for the denial?
6. Describe and provide a copy of the company's policies and procedures relating to protecting the privacy of a customer's account information and other personal identification information that may be provided by the customer in conjunction with applying for, or transferring utility service, or paying utility bills. In particular, describe the security measures or procedures that are in place to protect or secure personal information customers provide to the company.
7. For the calendar year ending December 31, 2003, provide the following information related to establishing or transferring customer accounts:
(a) Total number of new accounts.
(b) Total number of transferred accounts.
(c) Total number of new accounts for which identity of consumer was verified by:
i. Credit history check.
ii. Government-issued photograph identification card, such as a driver's license, student identification card, employee identification card.
iii. Government issued non-photograph identification card, such as a library card, voter registration card.
iv. Other form of identification, such as credit card, automobile club service card, student identification card, employee identification card.
(d) Total number of transferred accounts for which identity of the consumer was verified by:
i. Credit history check.
ii. Government-issued photograph identification card, such as a driver's license, student identification card, employee identification card.
iii. Government issued non-photograph identification card, such as a library card, voter registration card.
iv. Other form of identification, such as credit card, automobile club service card, student identification card, employee identification card.
8. Provide the address and hours of operation of each company office that is open to the public where a consumer can establish or transfer a service account in person. The term ''company office'' includes an office that is operated by an agent of the company. Identify each company office that is operated by contracted agents.
9. Provide the total amount of costs attributable to identity theft involving customer accounts for each of the following calendar years:
(a) For the year ending December 31, 2000.
(b) For the year ending December 31, 2001.
(c) For the year ending December 31, 2002.
(d) For the year ending December 31, 2003.
If the company keeps statistics by fiscal year, please provide the above information for the immediate past four fiscal years.
Explain how the company identifies and tracks costs that can be attributed to identity theft. The term ''costs'' is defined to include all expenditures made in investigating and verifying identity theft claims.
10. Provide the total amount of losses attributable to identity theft involving customer accounts for each of the following calendar years:
(a) For the year ending December 31, 2000.
(b) For the year ending December 31, 2001.
(c) For the year ending December 31, 2002.
(d) For the year ending December 31, 2003.
If the company keeps statistics by fiscal year, please provide the above information for the immediate past four fiscal years.
The term ''losses'' is the dollar amount of uncollected charges for stolen service as a result of identity theft. Explain how the company identifies and tracks losses that can be attributed to identity theft. Also, explain how much of the company's active debt and write-offs, expressed in total dollars and as a percentage of the whole, are directly attributable to identity theft. Please provide figures for the company's gross debt and for gross write-offs for comparison to the percentages attributable to identity theft.
11. Provide a copy of the company's current procedures for conducting internal investigations related to alleged customer identity theft by a company employee. Provide a copy of the final report on each internal investigation of alleged customer identity theft by a company employee that was conducted since January 1, 2000. Identifying personal information for the employee and customer must be redacted from each report.
12. Provide a copy of the company's current procedures for investigating customer allegations of identity theft relating to a utility service account. Provide a copy of the final report on each such investigation conducted since January 1, 2000. Identifying personal information for the customer must be redacted from each report.
13. Provide the total number of internal investigations of alleged customer identity theft by company employee conducted by the company for each of the following calendar years:
(a) For the year ending December 31, 2000.
(b) For the year ending December 31, 2001.
(c) For the year ending December 31, 2002.
(d) For the year ending December 31, 2003.
Indicate the number of internal investigations that are currently in progress.
14. Provide the total number of investigations of customer allegations of identity theft conducted by company for each of the following calendar years:
(a) For the year ending December 31, 2000.
(b) For the year ending December 31, 2001.
(c) For the year ending December 31, 2002.
(d) For the year ending December 31, 2003.
Indicate the number of investigations that are currently in progress.
15. Identify those Commission regulations that may create an opportunity for identity theft. Explain in detail how each regulation may contribute to the identity theft, and propose amendments to correct the problem.
ATTACHMENT B 
ATTACHMENT C 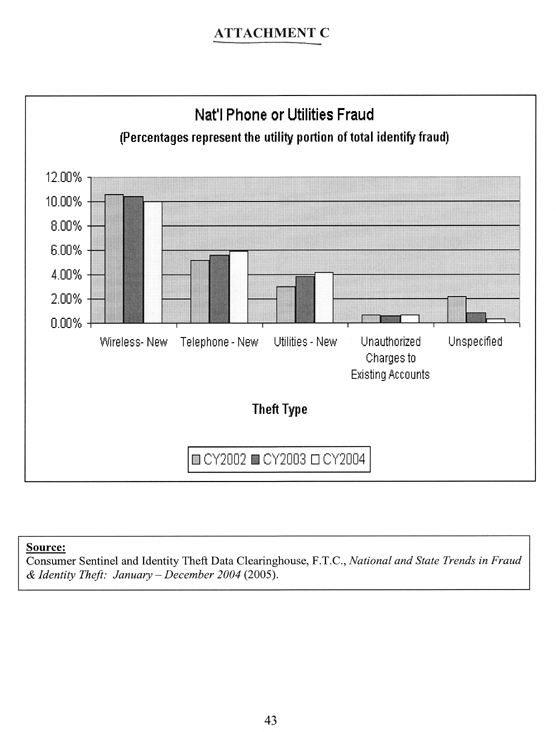
ATTACHMENT D 
[Pa.B. Doc. No. 05-1880. Filed for public inspection October 7, 2005, 9:00 a.m.] _______
1 Rules promulgated under the Fair Credit Reporting Act require notification of consumers following a security breach.
2 For example, California, Arkansas, Connecticut, Florida, Nevada and Texas.
3 We note that the General Assembly recently adopted a Resolution to establish a committee to investigate and review the policies, procedures and practices of various Commonwealth Agencies, authorities, boards, commissions, councils, departments and offices and the entities they license or regulate to protect the personal health, financial and other sensitive data of Pennsylvania citizens. See House Resolution 351.
4 One utility suggested that 52 Pa. Code § 64.32 be amended to remove reference to the ''applicant's social security number'' so that this number is not made available. Another company proposed changes to 52 Pa. Code § 64.32 to provide the utility with the ability to require five pieces of identification for applicants, including a requirement that applicants provide a social security number without restriction.
5 In their respective responses, utilities referenced Commission regulations such as 52 Pa. Code §§ 56.2; 59.26; 56.16; 56.16; 56.33; 65.72; 56.131; and 64.61.
6 Specifically, section 6 of Act 201, Act of November 30, 2004, P. L. 1578, effective Dec. 14, 2004, provides: ''The Pennsylvania Public Utility Commission shall amend the provisions of 52 Pa. Code Ch. 56 to comply with provisions of 66 Pa.C.S. Ch 14. . . .''
7 February 2005--Choice Point, Inc. reported that consumer profiles of 145,000 compromised. April 2005--LexisNexis announced personal information of 310,000 accessed through identity theft. May 2005--Time Warner reported that personal data of 600,000 current and former employees compromised. June 2005--Card Systems indicated that as a result of a security breach the credit information of approximately 40million cardholders was compromised.
8 In a June 2005 article, the Wall Street Journal reported that stock ratings fell for companies after reported data breach incidences. In recent publications, identity theft has been referred to as the next wave of corporate liability.
9 See Investigation Order at 2. The Order references the Commission's decision in Donna MacDougall v. Verizon North, Inc., F-01339719 (Order entered Aug. 23, 2004). In that case, an individual fraudulently established telephone service in the complainant's name. The Commission found that the complainant offered sufficient evidence to support a finding of identity theft based on the police report she filed and her testimony that she discontinued service to the address in question and never resided there. In the Order, the Commission explained that the proceeding highlighted the need to explore methods of ensuring protections for consumers and utilities with regard to identity theft and further stated, ''it is appropriate for the Commission to open an investigation, under a separate docket, to address the broader issue of identity theft and how it impacts utility service in Pennsylvania.''
10 See e.g., 52 Pa. Code §§ 56.31, et seq.; 52 Pa. Code §§ 64.31, et seq.
11 66 Pa.C.S. §§ 501, 504, 505, and 506.
12 Steven F. Miller, Someone Out There is Using Your Name: A Basic Primer on Federal Identity Theft Law, Fed. Law., Jan. 11, 2003, at 11.
13 Sean B. Hoar, Identity Theft: The Crime of the New Millennium, 80 Or. L. Rev. 1423 (2001).
14 Synovate, F.T.C., Identity Theft Survey Report 9, 30 (2003), available at http://www.ftc.gov/os/2003/09/synovatereport.pdf (hereafter ''F.T.C. 2003 Report''). The 4.6 percentage amount equates to 9.91 million individuals.
15 Treasury Inspector General for Tax Admin., The Internal Revenue Service's Individual Taxpayer Identification Number Creates Significant Challenges for Tax Administration, at 10 (Jan. 2004).
16 18 Pa.C.S. § 4120.
17 Holly K. Towle, Identity Theft: Myths, Methods, and New Law, 30 Rutgers Computer & Tech. L. J. 237, 241 (2004); S. Rep. No. 105-274, at 6 (1998).
18 Id.
19 F. T. C. 2003 Report at 28-29.
20 U. S. Gen. Accounting Office, Identity Theft: Greater Awareness and Use of Existing Data are Needed 1,6 (June 2002).
21 18 U.S.C. § 1028(a).
22 Id.
23 Pub. L. 108-159, 117 Stat. 1952. FACT Act amended the Fair Credit Reporting Act of 1970 (FCRA), which regulated the obligations of credit bureaus and those supplying information to them.
24 Pub. L. 108-275.
25 Consumer Sentinel and Identity Theft Data Clearinghouse, F.T.C., National and State Trends in Fraud & Identity Theft: January--December 2004, (2005).
26 Id.
27 Id. at 3.
28 Id.
29 Id. at 10. See, e.g., Verizon Pennsylvania Inc. and Verizon North Inc. (Verizon)-- Pennsylvania Office of Consumer Advocate (OCA) Settlement Agreement, available on the OCA website at www.oca.state.pa.us. In the settlement, the OCA and Verizon want to resolve all pending complaints before the Commission by Verizon customers regarding Verizon Long Distance international toll charges associated with modem hijacking, including those formal complaints in which the OCA has intervened, and to avoid future modem hijacking litigation.
30 Id. at 10.
31 Id. at 54.
32 Id. at 12.
33 Id. at 14.
34 Id. at 54.
35 F.T.C. 2003 Report at 4.
36 Id. at 7.
37 Identity Theft Data Clearinghouse, F.T.C., Identity Theft Victim Complaint Data: Figures and Trends in Pennsylvania--January 1--December 31, 2003, Figure 2 (2003).
38 Id.
39 Id., Figure 4a.
40 Id., Figure 5.
41 Holly K. Towle, Identity Theft: Myths, Methods, and New Law, 30 Rutgers Computer & Tech. L. J. 237, 240-241 (2004).
42 Comments of the Pennsylvania Telephone Association, M-00041811 at 2, 3.
43 Question 15 of the Order asked the utilities to respond to the following: ''Identify those Commission regulations that may create an opportunity for identity theft. Explain in detail how each regulation may contribute to the identity theft, and propose amendments to correct the problem.''
44 The offense of ''identity theft'' is defined as ''. . . the possession or use, through any means, of identifying information of another person without the consent of that other person to further any unlawful purpose.'' 18 Pa.C.S. § 4120.
45 See 52 Pa. Code § 56.2(definitions) and 52 Pa. Code § 64.2 (definitions).
No part of the information on this site may be reproduced for profit or sold for profit.This material has been drawn directly from the official Pennsylvania Bulletin full text database. Due to the limitations of HTML or differences in display capabilities of different browsers, this version may differ slightly from the official printed version.